DefendX Control
Control storage resources and secure corporate file assets. Think of us as the camera in the office supply room.
.png)
Right now, a storm of insider threats is brewing – right under your nose.
Your storage resources and file assets are being exposed to waste, theft, loss and misuse by the very people who are responsible for taking care of those resources and files. Left alone, those threats result in revenue loss and put risk at the forefront. It’s your job to know it and stop it.

DefendX Control gives you the power to:
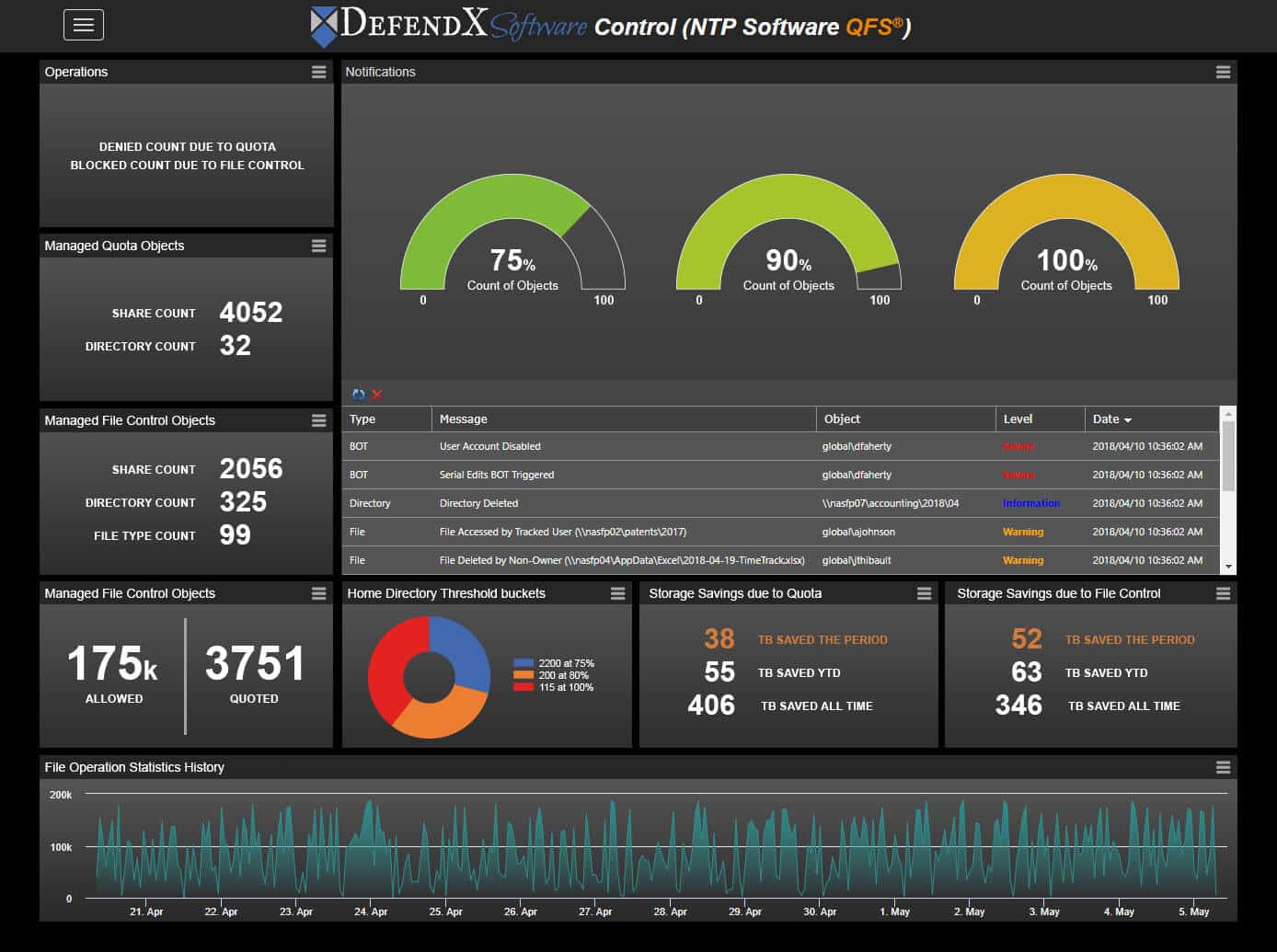
- Manage storage consumption through hard and soft user quota policies
- Prevent unwanted files from entering your environment through advanced file blocking policies
- Maintain policy governance through comprehensive discovery, real-time alerts, and automated quarantine and removal actions
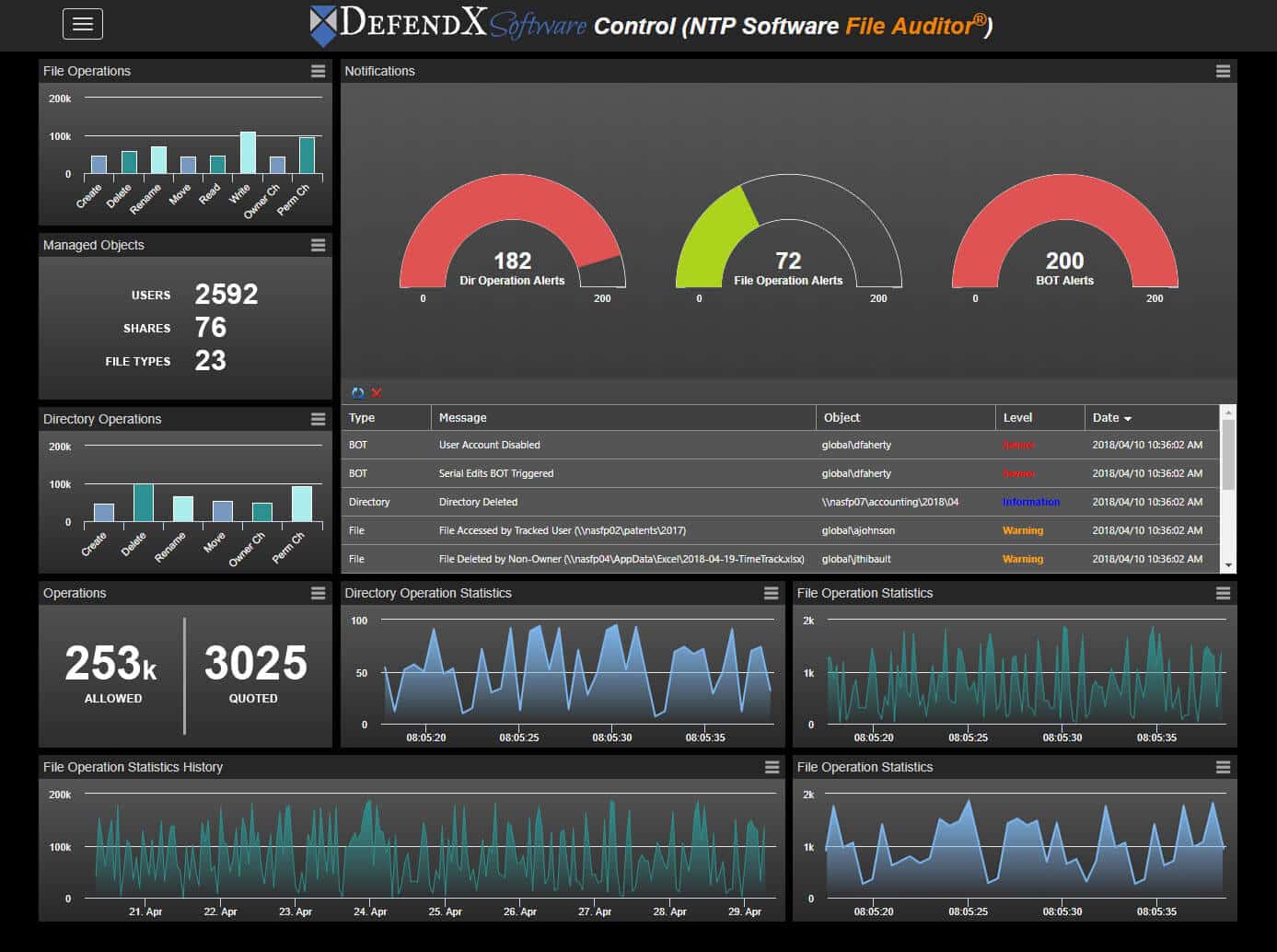
- Enable legal holds and investigations through extensive audit trails
- Protect against theft or other malicious activities through file activity and user behavior monitoring
- Demonstrate corporate and regulatory compliance through comprehensive policy and audit reporting
DefendX Control Features

Governance
Enforce file management policies with automated alerts and actions.
Monitoring
Watch users and file locations for abnormal behavior.

Auditing
Enable complete audit trails for file and user activity.

Legal Hold
Enforce legal hold orders by restricting file access and activity.

Blocking
Prevent unwanted file types from being stored on corporate file shares.

Quotas
Restrict storage resource consumption by user or organizational department.
DefendX Control Resources
From technical documents to white papers, we have everything you need to learn more about DefendX Control and all of our other products and solutions.
Read our blog post here to see how DefendX Software Control helps you implement a good file data management system.

Get Started Today
Don’t let chaos and risk hijack your valuable storage resources and hold your business hostage. Find out how to better understand your corporate file repository, keep it space efficient, and secure important files from insider threats.


.png)