DefendX White Papers
Click on a white paper below to download PDF
Ransomware – How To Create a Proactive Protection File Strategy
IT needs a proactive way to stop ransomware. It’s here to stay. Most ransomware countermeasures are reactive. The damage is done before IT can deploy their reactive countermeasures. When ransomware gets through an organization’s defenses, it starts to encrypt data, and the race is on. How much data will the ransomware encrypt before IT can disconnect the infected systems?
The Data Security 8-Step Checklist
Your stored file data is critical to running your business. Yet with potentially billions of files in storage, have you taken every precaution to improve your overall data security and implement the right data management policies? The checklist covers all the basics to help you mitigate your risk. With file auditing software and using these tips, your primary storage will have improved monitoring and be more resilient.
Understanding Stubs Reference Guide
Now that file data archiving is at the top of everyone’s list, it is important to have a working understanding of its core technology so that you don’t miss opportunities and you are able to make the right choices for your organization. In this regard, one of the most important things to understand is the variety of possible stubs – and whether you should use them at all.
Finding the Risks and Opportunities in Your Storage
In an organization of any size, it is simply not possible to figure out what is important and what your storage management priorities should be by manually analyzing the environment. A terabyte of data contains tens of thousands of directories and millions of files. Multiple terabytes spread across a number of systems that grow and change every day is something that defies human analysis. Only a computer program designed specifically for this purpose can give you the information you need. The purpose of this White Paper is to show you what to look for and to help you understand the risks and opportunities that the information about your storage environment can expose.
File Data Storage for Financial Services: What is the True Cost?
A Comprehensive Guide to File Management
Stubs – The Good, the Bad and the Ugly
Reducing Primary Storage Costs and Complexity with DefendX Software Mobility
Allocating resources to high-cost storage for low-use data doesn’t make sense. Most organizations would rather match storage to data and use the saved budgetary resources for other projects. DefendX Software Mobility™ makes it easy for you to find and migrate data automatically to the most appropriate storage tier, ensure proper archiving of valuable data, meet compliance and governance requirements, and ensure proper data protection.
Backups, Tiering, and Archiving: Do I Need Them All?
Backups, tiering, archiving, replication, encryption, compression, geo-fencing, dedupe: managing file data today is a lot more complicated than it used to be. The purpose of this white paper is to help you understand how backup, tiering, and archiving technologies differ and how they work together to meet your business needs in a cost effective manner.
Tiering to Maximum Benefit
It’s seductively easy to focus on cost per gigabyte in any discussion about tiering. Given that today’s disk drives are often the same across platforms, this isn’t where the real benefits are to be found. This White Paper will show you how to achieve a superior result, reducing both your cost and risk.
Skyrocket Savings with Read-Only Tier 2
Do You Need A Storage Management Policy
Companies vary greatly in their approach to storage management. Most organizations have some policy; a few have none. Of those with formal policies, many use third-party technology as part of their efforts. The purpose of this paper is to help you understand why they went down this path; how they succeeded; and whether, like them, you should consider storage resource management.
How to Choose the Right Tiering Solution
Improve NetApp Storage Efficiency with Directory-Based and Group-Based Quotas and Policies
What this means is that if we want to improve the cost-effectiveness of our storage, then how we manage file data is the place to look. By choosing NetApp as your host platform, you have already taken one of the most important steps in implementing a cost-effective solution. The purpose of this paper is to help you increase the return on your investment by showing you Best Practice techniques for managing the data stored on your NetApp storage systems.
Profiting with DefendX Software’s Technology
Protecting the Value of Your Business Data with DefendX Software File Intelligence
Establishing a comprehensive data monitoring plan for your organization is a key part of securing the value of your stored data, but manual methods of data monitoring are simply unfeasible in most environments. This paper shows you how to use automated data monitoring software to expose and reduce the security risks in your data.
Understand the User Aspect of Storage Management
The storage hosted on your network is a service you provide to your end users. The right way to think about it and its management is not as hardware, but as a consumer service offering. Once you think about it this way, you manage it differently. The keys to success in running this service offering are to see things from the client’s perspective, and keep the client informed and engaged throughout the process. This paper will help you understand how to do this.
What's So Special About DefendX Software's Mobility?
DefendX Software Mobility™ gives you important features and benefits that go beyond ordinary file archiving. In fact, several of these features are patent protected and thereby available nowhere else. Taken together, these abilities make the choice of tiering software easy. Only one product meets all or most of a typical organization’s needs. Let’s look at some specifics.
What Does DefendX Software Mobility Offer You?
What’s So Smart About Smart Migration?
With hardware upgrades staring us in the face, we all need to think about Migrations sooner or later. But with storage estates growing larger every year, traditional means of Migration no longer cut it. So what to do? DefendX Software Smart Migration™ is the first program to meaningfully automate parts of the Migration process that are simply impossible to do by hand.
Storage and Your Legal Obligations
Storage management no longer means simply managing backups or keeping your servers online. In today’s legal environment, storage administrators need to pay close attention to what is stored on their networks and how it’s being used. This paper provides a brief description of some of the key laws and regulations that may affect your storage environment, along with some best practices for how to achieve compliance in your organization.
Six Easy Ways to Control Storage Growth
What people often miss in all the hype surrounding these new technologies is that there are very effective ways to control storage growth that have existed for years and that don’t require rebuilding your current infrastructure or need new hardware platforms. Many companies have used these ‘legacy’ techniques successfully for years. The purpose of this White Paper is to highlight these methods and to explain their benefits and how you can profit from them.
Need more support?
Try our Support Portal.
If you need technical assistance for your DefendX (formerly NTP Software) products, we are here to help.
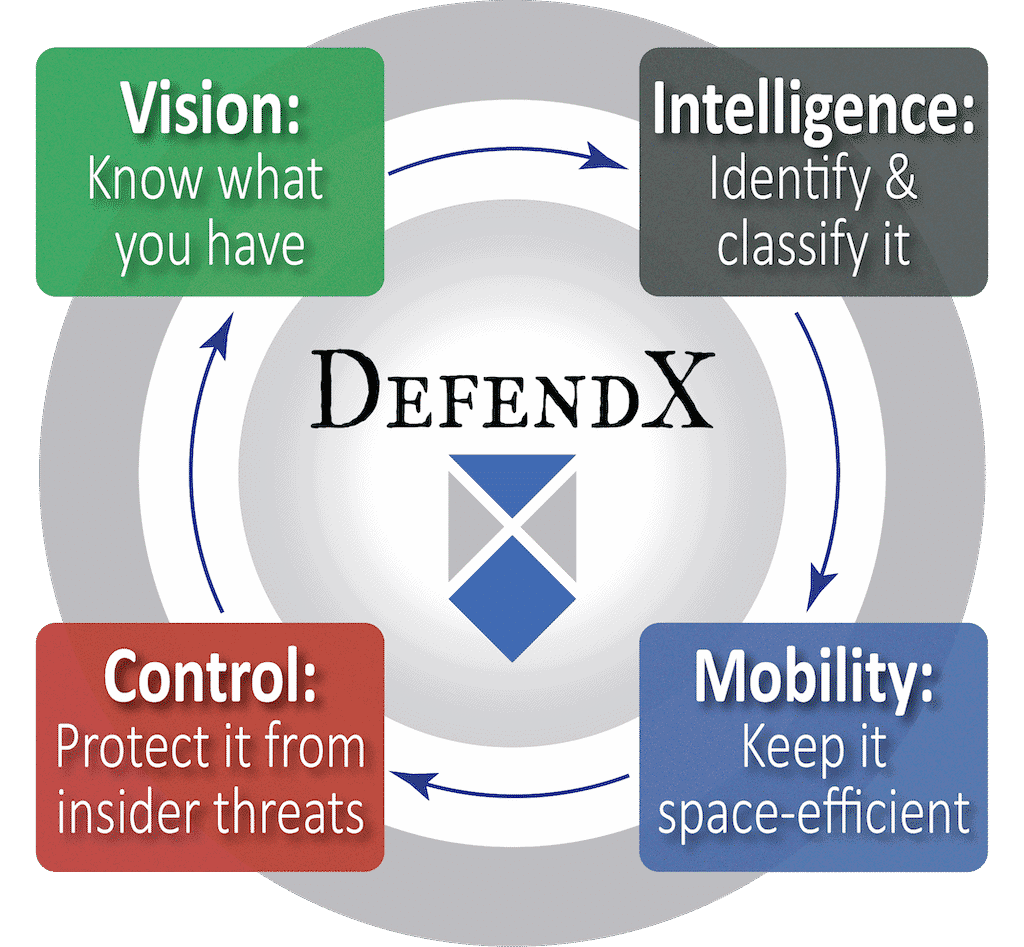

Get Started Today
Don’t let chaos and risk hijack your valuable storage resources and hold your business hostage. Find out how to better understand your corporate file repository, keep it space efficient, and secure important files from insider threats.





.jpg)













.jpg)


